

Xcitium Blog

While we may think of the online world as a safe and nice place of fun and recreation, the reality is very far from it. We are surrounded by constant and ever-present threats online. We must be careful about how we use our gadgets and devices. It is important that we become curious about the […]

The modern workplace demands an inevitable need for mobility. Today’s business trends are quite faster and there is always a need for quick response – Mobile devices help to enhance the productivity and efficiency of any MDM endpoint business making the users omnipresent. However, with pros on one side, there are always some disadvantages to […]

Define Ransomware Attack: Since WannaCry caused a global outcry, the average computer user has learned the term— “ransomware attack”. Ransomware attack is not new. It’s been here for ages. The first known case was Joseph Popp, an evolutionary biologist who developed the AIDS Trojan. Any computer infected with the Trojan was asked to pay $189 […]

Did you know that small businesses in the United States lose up to 75 billion dollars annually to ransomware cyber attack? This is according to a survey by Datto. These attack happen multiple times in a day. Large companies are also targeted by ransomware cyber attack. For instance, FedEx lost an estimated $300 million in […]

In today’s digital era where sensitive data gets stored electronically in computer servers, organizations can no longer operate without some form of Importance Endpoint Protection. The costs associated with network downtime or stolen data resulting from malicious attacks significantly outweigh the cost of maintaining up-to-date Importance Endpoint Protection software. Endpoint security software is fundamentally different […]

It is common knowledge that malware attacks corrupt files and sometimes destroys them completely. However, the reverse is the case with What ransomware attacks do. Here is the scenario of What Ransomware Attack Does to your computer What Ransomware Does and What Is Ransomware? Ransomware is another malware type that infects computers. But unlike other […]

Because ransomware is an inventive malware type that uses elaborate cop-out techniques, it’s a lot more difficult and challenging for ordinary antivirus programs to find. So considering how IT experts continue to up their ways in finding ransomware removal solutions, it’s only right that we improve our individual ransomware detection techniques, too. Precisely why for […]
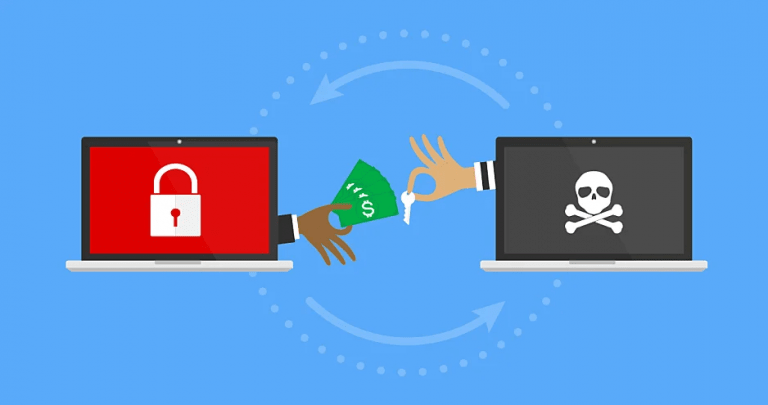
Threatware, spyware, malware, are all terms used to describe malicious codes that harm your computers, steal your information, or hold your computer to a threatware. These ransomware threatware malicious codes are spread by cybercriminals with the intent of wreaking havoc to your system. In recent times, ransomware has been in the news as one of […]

Ransomware Threats The Ransomware attack is a type of malware that threatens to erase or deny access to data once it has taken over your computer. The attacker demands ransom, usually through cryptocurrency, in order to restore your access to the files. Owing to the growing trend of ransomware threats, enterprises and their data have […]
Bloomfield, NJ 07003Tel: +1 (888) 551-1531Tel: +1 (973) 859-4000Fax: +1 (973) 777-4394


