

Xcitium Blog

What Is Ransomware Meaning?: The majority of the malware that trouble computer users operate in a like manner. For instance, worms, Trojans, and viruses inhabit your computer and cause a bug or corrupt all files leading to data damages. The reverse is the case with ransomware, which is another type of malware. Although the mode […]
How Can Ransomware Spread?: Many years ago, in 1989, precisely—a seminar organized by the world health organization witnessed attendees’ data restricted after using an AIDS guide diskette on their computers ransomware spread. This diskette was loaded with malicious codes instead of the information it claimed to have about AIDS spread. The creator of the malware, […]

How To Get Rid of Virus?: When your PC is infected with a foreign body, it would show up the following signs and symptoms When the computer runs slow Annoying pop-ups which are hard to get rid of a virus Constant sound of the hard drive Blue Screen death If you find any of the […]
What Is Vulnerability Assessment? The name suggests is the process of recognizing, analyzing, and ranking vulnerabilities in computers and other related systems to equip the IT personnel and management team with adequate knowledge about prevailing threats in the environment. With the appropriate information at hand, the risk factors can rightly be understood, and the required measures can […]

What is Zeus Malware?: Zeus malware (a Trojan Horse malware) is also known as Zeus virus or Zbot. This malware runs on different versions of Microsoft Windows and is supposed to carry out malicious activities at the victim’s computer. The reason for making the Zeus malware banking trojan was to steal banking records by man-in-the-browser keystroke […]

How To Get Rid of Crypto Locker Ransomware? It is no doubt that ransomware and its many variants have become a nuisance to our digital online lives. Our privacy and security are threatened because of these threats in the cyber community. One way to arm ourselves against these threats is to be informed. This article […]

What Is Firewall Security?: In the computing world, the terminology firewall security refers to a network device that blocks certain kinds of network traffic. What Is Firewall Security and What Does A Firewall Security Do? Actually, it acts as a barrier between a trusted and an untrusted network. The firewall security wall can be compared to […]
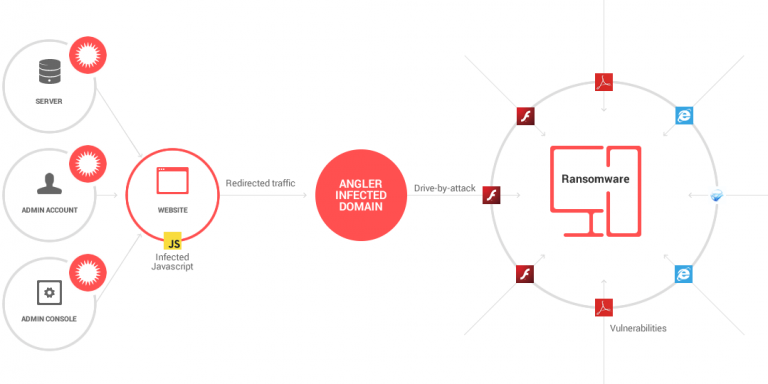
How Fast Does Ransomware Work?: It is no longer news that ransomware is presently one of the most troublesome and challenging issues malware threatening businesses and individuals. Ransomware attacks in the United States alone cost businesses over $7.5 billion in 2019. The most recent ransomware attacks—and one of the most devastating in recent history was the WannaCry […]

IT Endpoint Security: Most security groups work under the conviction that rapid remediation an episode levels with compelling reaction. All things considered, in IT endpoint security divisions, where data security has its underlying foundations and where numerous security specialists have gained immense technical knowledge, this is the means by which achievement is estimated: the quicker […]
Bloomfield, NJ 07003Tel: +1 (888) 551-1531Tel: +1 (973) 859-4000Fax: +1 (973) 777-4394


